Page 9 - FNSV_Catalog_01_211213
P. 9
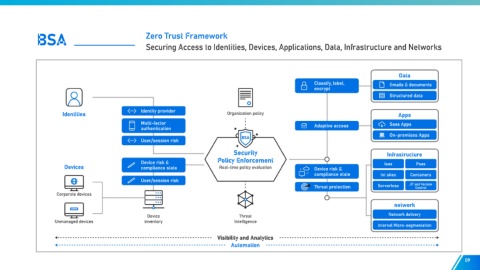
BSA Zero Trust Framework
Securing Access to Identities, Devices, Applications, Data, Infrastructure and Networks
Data
Classify, label, Emails & documents
encrypt
Structured data
Identities Identity provider Organization policy Apps
Multi-factor Adaptive access Saas Apps
authentication
On-premises Apps
User/session risk
Security Infrastructure
Device risk & Policy Enforcement Iaas Paas
Devices compliance state Real-time policy evaluation Device risk &
compliance state Int sites Containers
User/session risk
Threat protection Serverless JIT and Version
Control
Corporate devices
network
Device Threat Network delivery
Unmanaged devices inventory Intelligence
Internal Micro-segmentation
Visibility and Analytics
Automation
09