Page 56 - cyber law new
P. 56
Cyber Crime and Law verification and presentation of e-evidence has been done and present in court of law
for further proceedings. The collection of electronic evidence must be followed with
five basic rules as follows:
Notes First one is admissibility which is the most basic rule to be followed in court
of law.
Evidence should be authentic, if it should not tie with the incident positively,
then it should be difficult to prove anything with the use of that evidence.
It should be complete and reliable. Since, an evidence collection and analysis
procedures must not cast doubt on the authenticity of the evidences.
Lastly, the evidence which is presented in front of jury should be understandable
and believable.
While, if it should be followed with general procedure of collecting and analyzing
evidence. Then there are four step procedures which an official have to be followed
during the time of investigation i.e. identification of evidence, preservation of evidence,
analysis of evidence and finally presentation of evidence. However, if we deal with the
collection procedure of digital or electronic evidence then in this situation an official
follows such steps i.e.
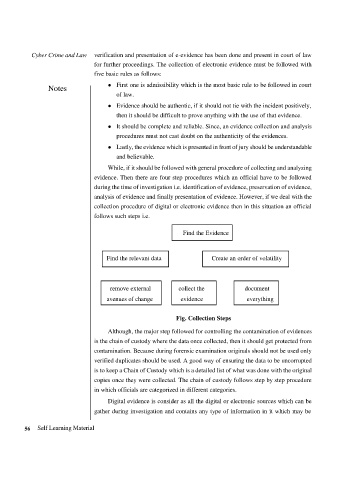
Find the Evidence
Find the relevant data Create an order of volatility
remove external collect the document
avenues of change evidence everything
Fig. Collection Steps
Although, the major step followed for controlling the contamination of evidences
is the chain of custody where the data once collected, then it should get protected from
contamination. Because during forensic examination originals should not be used only
verified duplicates should be used. A good way of ensuring the data to be uncorrupted
is to keep a Chain of Custody which is a detailed list of what was done with the original
copies once they were collected. The chain of custody follows step by step procedure
in which officials are categorized in different categories.
Digital evidence is consider as all the digital or electronic sources which can be
gather during investigation and contains any type of information in it which may be
56 Self Learning Material