Page 55 - CDSSa
P. 55
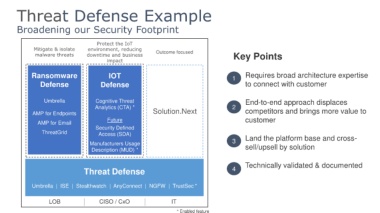
Threat Defense Example
Broadening our Security Footprint
Protect the IoT
Mitigate & isolate environment, reducing
malware threats downtime and business Outcome focused Key Points
impact
•
Ransomware IOT 1 Requires broad architecture expertise
Defense Defense to connect with customer
Umbrella Cognitive Threat • End-to-end approach displaces
Analytics (CTA) * 2
AMP for Endpoints Solution.Next competitors and brings more value to
Future customer
AMP for Email
Security Defined
ThreatGrid Access (SDA)
•
3 Land the platform base and cross-
Manufacturers Usage sell/upsell by solution
Description (MUD) *
• Technically validated & documented
Threat Defense 4
Umbrella | ISE | Stealthwatch | AnyConnect | NGFW | TrustSec *
LOB CISO / CxO IT
* Enabled feature