Page 15 - Interact Company Profile
P. 15
Security
Solutions
Interact can provide End to End security, our security solution philosophy for Security
solution is identifying security threats that challenge your organization and provide
the appropriate solutions for them.
To this Target, we have partnered with several specialized Security vendors to
provide best of breed solutions to our clients.
We aim to offer a variety of products and services that fit almost any budget and
fulfill the needs of organizations regardless of their size.
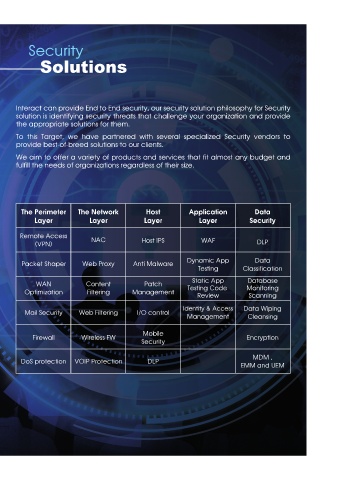
The Perimeter The Network Host Application Data
Layer Layer Layer Layer Security
Remote Access NAC
(VPN) Host IPS WAF DLP
Packet Shaper Web Proxy Anti Malware Dynamic App Data
Testing Classification
WAN Content Patch Static App Database
Optimization Filtering Management Testing Code Monitoring
Review
Scanning
Identity & Access Data Wiping
Mail Security Web Filtering I/O control
Management Cleansing
Mobile
Firewall Wireless FW Encryption
Security
MDM ,
DoS protection VOIP Protection DLP
EMM and UEM