Page 13 - PowerPoint Presentation
P. 13
Chapter 1
SECURITY AND RISK MANAGEMENT (Part 1)
Learning Objectives
After the completion of the chapter, students will be able to:
1. elaborate the CIA triad elements of confidentiality, integrity, and availability.
2. explain how identification works.
3. discuss the process of authentication.
4. explain how authorization fits into a security plan.
5. explain the auditing process.
6. discuss the importance of accountability.
7. identify key security roles.
8. explain how layering simplifies security
9. explain the concept of abstraction, data hiding, and the need for encryption
10. discuss why and how data is classified.
Security Governance Through Principles and Policies
A. Understand and Apply Concepts of Confidentiality, Integrity, and Availability
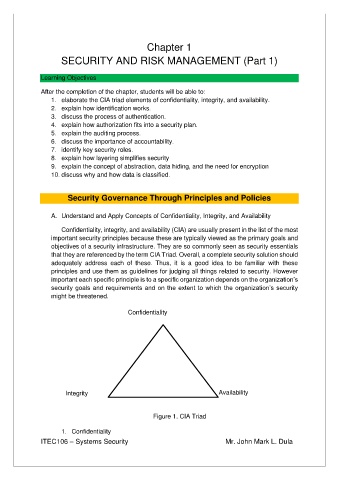
Confidentiality, integrity, and availability (CIA) are usually present in the list of the most
important security principles because these are typically viewed as the primary goals and
objectives of a security infrastructure. They are so commonly seen as security essentials
that they are referenced by the term CIA Triad. Overall, a complete security solution should
adequately address each of these. Thus, it is a good idea to be familiar with these
principles and use them as guidelines for judging all things related to security. However
important each specific principle is to a specific organization depends on the organization’s
security goals and requirements and on the extent to which the organization’s security
might be threatened.
Confidentiality
Integrity Availability
Figure 1. CIA Triad
1. Confidentiality
ITEC106 – Systems Security Mr. John Mark L. Dula