Page 320 - ITGC_Audit Guides
P. 320
What type of testing is performed (penetration, access, tracked changes, etc.)?
How is cybersecurity risk monitored for those who have functional access to critical
information?
Management should consider performing a business impact analysis to classify, prioritize, and
document the population of critical systems, data, and resources, if such considerations are
not already documented in a business continuity or disaster recovery plan. The CAE can utilize
the business impact analysis results to determine if the internal audit plan sufficiently covers
systems that contain critical information. The CAE can then disclose to the board the areas
where assurance may or may not be currently provided and the plans to provide coverage.
An Approach for Assessing Cybersecurity Risks and Controls
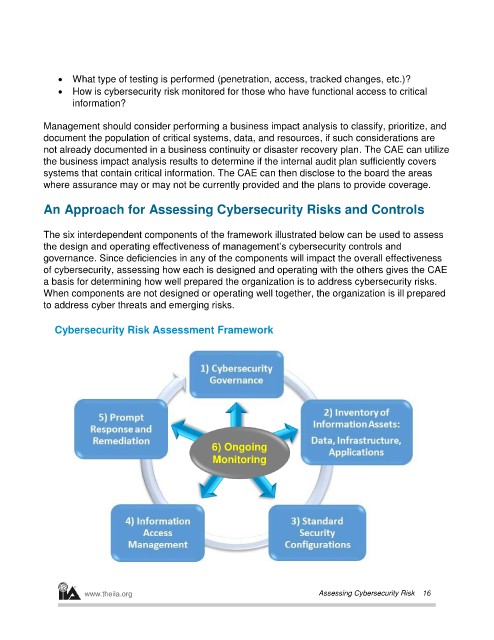
The six interdependent components of the framework illustrated below can be used to assess
the design and operating effectiveness of management’s cybersecurity controls and
governance. Since deficiencies in any of the components will impact the overall effectiveness
of cybersecurity, assessing how each is designed and operating with the others gives the CAE
a basis for determining how well prepared the organization is to address cybersecurity risks.
When components are not designed or operating well together, the organization is ill prepared
to address cyber threats and emerging risks.
Cybersecurity Risk Assessment Framework
6) Ongoing
Monitoring
www.theiia.org Assessing Cybersecurity Risk 16