Page 9 - Security Threats new3
P. 9
II. SPOOFING
Any kind of behaviour where an attacker mask as an authentic user or a device
to secure something
beneficial or crucial
information for their gain
is called spoofing.
There are various
kinds of spoofing such as
website spoofing, E-
mail spoofing, and IP
spoofing. Other common
methods include ARP
(Address resolution
protocol) spoofing
attacks and DNS
(Domain name) server
spoofing attacks.
An E-mail spoofing targets the user while an IP spoofing is predominantly
targeted at a network.
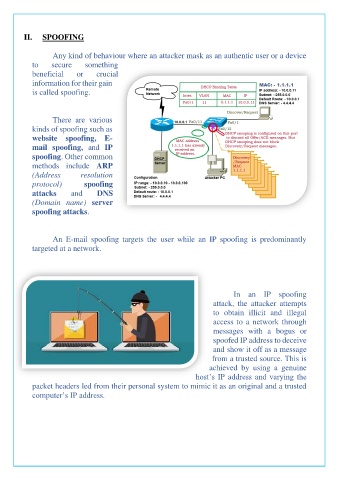
In an IP spoofing
attack, the attacker attempts
to obtain illicit and illegal
access to a network through
messages with a bogus or
spoofed IP address to deceive
and show it off as a message
from a trusted source. This is
achieved by using a genuine
host’s IP address and varying the
packet headers led from their personal system to mimic it as an original and a trusted
computer’s IP address.