Page 7 - Meet the dynamic needs of a remote workforce_Neat
P. 7
Leverage granular access
controls and simplified
policy management
Securely authenticate users and provision
access from anywhere.
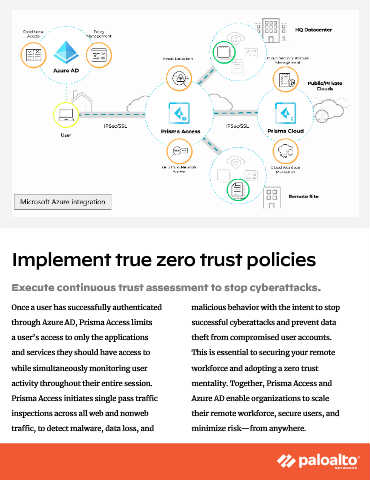
Remote work requires fast and reliable access to company
resources. The integration between Prisma Access and Azure AD
allows companies to seamlessly manage access control policies
for all users regardless of their location. Users first authenticate
through Azure AD, which selectively provisions access using
advanced security measures like Conditional Access policies. Implement true zero trust policies
This ensures that applications are provisioned to the right
users depending on user attributes, their device, geographic
Execute continuous trust assessment to stop cyberattacks.
location, and user risk. Once authenticated, Prisma Access
Once a user has successfully authenticated malicious behavior with the intent to stop
then inspects the security posture of user devices and provides
through Azure AD, Prisma Access limits successful cyberattacks and prevent data
secure, encrypted remote access to corporate resources—
a user’s access to only the applications theft from compromised user accounts.
enabling policy-controlled access to specific applications and
and services they should have access to This is essential to securing your remote
services. The need for multiple interfaces to access distributed
while simultaneously monitoring user workforce and adopting a zero trust
applications and services is eliminated, as corporate resources
activity throughout their entire session. mentality. Together, Prisma Access and
remain secure behind the global Prisma Access service edge.
Prisma Access initiates single pass traffic Azure AD enable organizations to scale
inspections across all web and nonweb their remote workforce, secure users, and
traffic, to detect malware, data loss, and minimize risk—from anywhere.
© 2020 Palo Alto Networks, Inc. and Microsoft Corporation. All rights reserved.