Page 164 - UKZN Proceedings of the Conference Report
P. 164
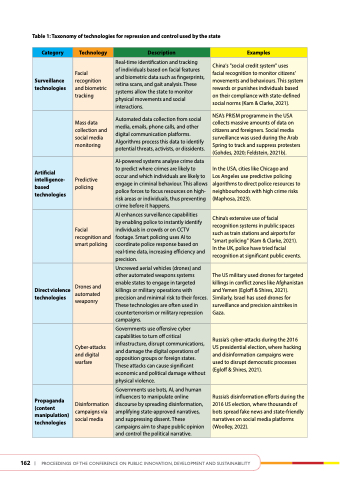
table 1: taxonomy of technologies for repression and control used by the state
Category
technology
description
examples
Surveillance technologies
Facial recognition and biometric tracking
Real-time identification and tracking
of individuals based on facial features and biometric data such as fingerprints, retina scans, and gait analysis. These systems allow the state to monitor physical movements and social interactions.
China's "social credit system" uses
facial recognition to monitor citizens' movements and behaviours. This system rewards or punishes individuals based on their compliance with state-defined social norms (Kam & Clarke, 2021).
Mass data collection and social media monitoring
Automated data collection from social media, emails, phone calls, and other digital communication platforms. Algorithms process this data to identify potential threats, activists, or dissidents.
NSA’s PRISM programme in the USA collects massive amounts of data on citizens and foreigners. Social media surveillance was used during the Arab Spring to track and suppress protesters (Gohdes, 2020; Feldstein, 2021b).
artificial intelligence- based technologies
Predictive policing
AI-powered systems analyse crime data to predict where crimes are likely to occur and which individuals are likely to engage in criminal behaviour. This allows police forces to focus resources on high- risk areas or individuals, thus preventing crime before it happens.
In the USA, cities like Chicago and
Los Angeles use predictive policing algorithms to direct police resources to neighbourhoods with high crime risks (Maphosa, 2023).
Facial recognition and smart policing
AI enhances surveillance capabilities
by enabling police to instantly identify individuals in crowds or on CCTV footage. Smart policing uses AI to coordinate police response based on real-time data, increasing efficiency and precision.
China’s extensive use of facial recognition systems in public spaces such as train stations and airports for "smart policing" (Kam & Clarke, 2021). In the UK, police have tried facial recognition at significant public events.
direct violence technologies
Drones and automated weaponry
Uncrewed aerial vehicles (drones) and other automated weapons systems enable states to engage in targeted killings or military operations with precision and minimal risk to their forces. These technologies are often used in counterterrorism or military repression campaigns.
The US military used drones for targeted killings in conflict zones like Afghanistan and Yemen (Egloff & Shires, 2021). Similarly, Israel has used drones for surveillance and precision airstrikes in Gaza.
Cyber-attacks and digital warfare
Governments use offensive cyber capabilities to turn off critical infrastructure, disrupt communications, and damage the digital operations of opposition groups or foreign states. These attacks can cause significant economic and political damage without physical violence.
Russia’s cyber-attacks during the 2016 US presidential election, where hacking and disinformation campaigns were used to disrupt democratic processes (Egloff & Shires, 2021).
Propaganda (content manipulation) technologies
Disinformation campaigns via social media
Governments use bots, AI, and human influencers to manipulate online discourse by spreading disinformation, amplifying state-approved narratives, and suppressing dissent. These campaigns aim to shape public opinion and control the political narrative.
Russia’s disinformation efforts during the 2016 US election, where thousands of bots spread fake news and state-friendly narratives on social media platforms (Woolley, 2022).
162 | Proceedings of the conference on Public innovation, develoPment and sustainability