Page 5 - Information_Security_Program
P. 5
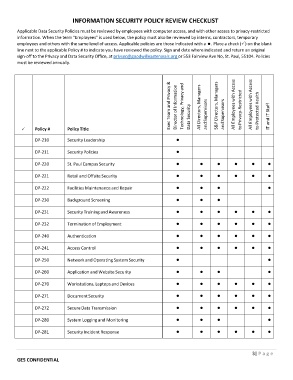
INFORMATION SECURITY POLICY REVIEW CHECKLIST
Applicable Data Security Policies must be reviewed by employees with computer access, and with other access to privacy‐restricted
information. When the term “Employees” is used below, the policy must also be reviewed by interns, contractors, temporary
employees and others with the same level of access. Applicable policies are those indicated with a . Place a check () on the blank
line next to the applicable Policy # to indicate you have reviewed the policy. Sign and date where indicated and return an original
sign‐off to the Privacy and Data Security Office, at privsec@goodwilleasterseals.org or 553 Fairview Ave No, St. Paul, 55104. Policies
must be reviewed annually.
Exec Team and Privacy & Director of Information Technology, Privacy and All Directors, Managers S&P Directors, Managers All Employees with Access All Employees with Access
to Privacy‐Restricted to Protected Health
Data Security and Supervisors and Supervisors IT and IT Staff
Policy # Policy Title
DP‐210 Security Leadership
DP‐211 Security Policies
DP‐220 St. Paul Campus Security
DP‐221 Retail and Offsite Security
DP‐222 Facilities Maintenance and Repair
DP‐230 Background Screening
DP‐231 Security Training and Awareness
DP‐232 Termination of Employment
DP‐240 Authentication
DP‐241 Access Control
DP‐250 Network and Operating System Security
DP‐260 Application and Website Security
DP‐270 Workstations, Laptops and Devices
DP‐271 Document Security
DP‐272 Secure Data Transmission
DP‐280 System Logging and Monitoring
DP‐281 Security Incident Response
3| P a g e
GES CONFIDENTIAL