Page 171 - ISCI’2017
P. 171
Generator 8-SHA-384 test results
1 The proportion passing
0,995
0,99
0,985
0,98
0,975
0,97
0,965
0,96
0,955
0 20 40 60 80 100 120 140 160 180 200
Test number
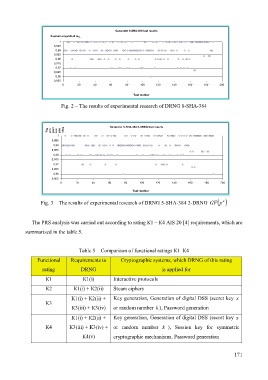
Fig. 2 – The results of experimental research of DRNG 8-SHA-384
Generator 5-SHA-384 2-DRNG test results
The pro port ion 1 pas sing
0,995
0,99
0,985
0,98
0,975
0,97
0,965
0,96
0,955
0 20 40 60 80 100 120 140 160 180 200
Test number
n
p
GF
Fig. 3 – The results of experimental research of DRNG 5-SHA-384 2-DRNG ( )
The PRS analysis was carried out according to rating К1 – К4 AIS 20 [4] requirements, which are
summarized in the table 5.
Table 5 – Comparison of functional ratings К1–К4
Functional Requirements to Cryptographic systems, which DRNG of this rating
rating DRNG is applied for
К1 К1(i) Interactive protocols
К2 К1(i) + К2(ii) Steam ciphers
К1(i) + К2(ii) + Key generation, Generation of digital DSS (secret key x
К3
К3(iii) + К3(iv) or random number k ), Password generation
К1(i) + К2(ii) + Key generation, Generation of digital DSS (secret key x
К4 К3(iii) + К3(iv) + or random number k ), Session key for symmetric
К4(v) cryptographic mechanisms, Password generation
171