Page 455 - From GMS to LTE
P. 455
Wireless Local Area Network (WLAN) 441
Access Auth. HLR/
Client
point server AuC
EAP MAP
EAPOL RADIUS SS-7
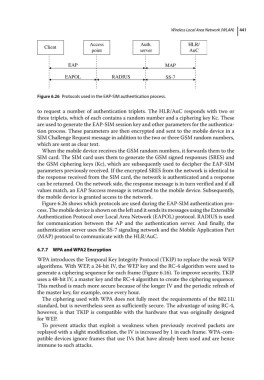
Figure 6.26 Protocols used in the EAP‐SIM authentication process.
to request a number of authentication triplets. The HLR/AuC responds with two or
three triplets, which of each contains a random number and a ciphering key Kc. These
are used to generate the EAP‐SIM session key and other parameters for the authentica-
tion process. These parameters are then encrypted and sent to the mobile device in a
SIM Challenge Request message in addition to the two or three GSM random numbers,
which are sent as clear text.
When the mobile device receives the GSM random numbers, it forwards them to the
SIM card. The SIM card uses them to generate the GSM signed responses (SRES) and
the GSM ciphering keys (Kc), which are subsequently used to decipher the EAP‐SIM
parameters previously received. If the encrypted SRES from the network is identical to
the response received from the SIM card, the network is authenticated and a response
can be returned. On the network side, the response message is in turn verified and if all
values match, an EAP Success message is returned to the mobile device. Subsequently,
the mobile device is granted access to the network.
Figure 6.26 shows which protocols are used during the EAP‐SIM authentication pro-
cess. The mobile device is shown on the left and it sends its messages using the Extensible
Authentication Protocol over Local Area Network (EAPOL) protocol. RADIUS is used
for communication between the AP and the authentication server. And finally, the
authentication server uses the SS‐7 signaling network and the Mobile Application Part
(MAP) protocol to communicate with the HLR/AuC.
6.7.7 WPA and WPA2 Encryption
WPA introduces the Temporal Key Integrity Protocol (TKIP) to replace the weak WEP
algorithms. With WEP, a 24‐bit IV, the WEP key and the RC‐4 algorithm were used to
generate a ciphering sequence for each frame (Figure 6.16). To improve security, TKIP
uses a 48‐bit IV, a master key and the RC‐4 algorithm to create the ciphering sequence.
This method is much more secure because of the longer IV and the periodic refresh of
the master key, for example, once every hour.
The ciphering used with WPA does not fully meet the requirements of the 802.11i
standard, but is nevertheless seen as sufficiently secure. The advantage of using RC‐4,
however, is that TKIP is compatible with the hardware that was originally designed
for WEP.
To prevent attacks that exploit a weakness when previously received packets are
replayed with a slight modification, the IV is increased by 1 in each frame. WPA‐com-
patible devices ignore frames that use IVs that have already been used and are hence
immune to such attacks.