Page 461 - From GMS to LTE
P. 461
Wireless Local Area Network (WLAN) 447
network load reaches the limit at which additional streams can no longer be supported.
These devices or applications can then choose to use a lower QoS class. For this pur-
pose, the 802.11e standard specifies an optional admission control mechanism. Through
the beacon frames, devices are informed if the AP requires access control for certain
QoS classes. If a device does not support the admission control functionality, it must
not use a QoS class for which admission control is used.
A device can register a new data stream by sending a Traffic Specification (TSPEC) in
an Add Traffic Specification (ADDTS) management message to the AP. The AP then
verifies whether the network can support the additional traffic load and either grants or
denies the request in a response message. The method by which the AP verifies that
enough bandwidth is available for the application is not defined. In practice, parameters
like the remaining bandwidth depend on the current reception conditions of all devices,
and therefore it is not straightforward to conclude whether an additional data stream
can still be supported when the network is already operating close to its maximum
capacity.
In addition to QoS functionality, 802.11e also introduces enhancements to improve
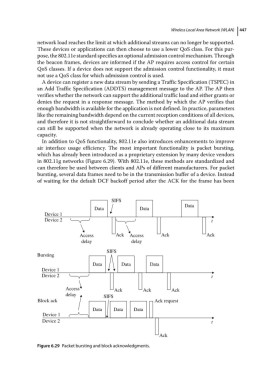
air interface usage efficiency. The most important functionality is packet bursting,
which has already been introduced as a proprietary extension by many device vendors
in 802.11g networks (Figure 6.29). With 802.11e, these methods are standardized and
can therefore be used between clients and APs of different manufacturers. For packet
bursting, several data frames need to be in the transmission buffer of a device. Instead
of waiting for the default DCF backoff period after the ACK for the frame has been
SIFS
Data
Data Data
Device 1
Device 2 t
Access Ack Access Ack Ack
delay delay
SIFS
Bursting
Data Data Data
Device 1
Device 2 t
Access Ack Ack Ack
delay SIFS
Block ack Ack request
Data Data Data
Device 1
Device 2 t
Ack
Figure 6.29 Packet bursting and block acknowledgments.