Page 438 - Using MIS
P. 438
406 Chapter 10 Information Systems Security
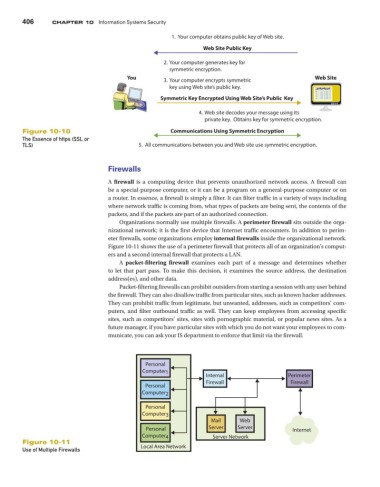
1. Your computer obtains public key of Web site.
Web Site Public Key
2. Your computer generates key for
symmetric encryption.
You 3. Your computer encrypts symmetric Web Site
key using Web site’s public key.
Symmetric Key Encrypted Using Web Site’s Public Key
4. Web site decodes your message using its
private key. Obtains key for symmetric encryption.
Figure 10-10 Communications Using Symmetric Encryption
The Essence of https (SSL or
TLS) 5. All communications between you and Web site use symmetric encryption.
Firewalls
A firewall is a computing device that prevents unauthorized network access. A firewall can
be a special-purpose computer, or it can be a program on a general-purpose computer or on
a router. In essence, a firewall is simply a filter. It can filter traffic in a variety of ways including
where network traffic is coming from, what types of packets are being sent, the contents of the
packets, and if the packets are part of an authorized connection.
Organizations normally use multiple firewalls. A perimeter firewall sits outside the orga-
nizational network; it is the first device that Internet traffic encounters. In addition to perim-
eter firewalls, some organizations employ internal firewalls inside the organizational network.
Figure 10-11 shows the use of a perimeter firewall that protects all of an organization’s comput-
ers and a second internal firewall that protects a LAN.
A packet-filtering firewall examines each part of a message and determines whether
to let that part pass. To make this decision, it examines the source address, the destination
address(es), and other data.
Packet-filtering firewalls can prohibit outsiders from starting a session with any user behind
the firewall. They can also disallow traffic from particular sites, such as known hacker addresses.
They can prohibit traffic from legitimate, but unwanted, addresses, such as competitors’ com-
puters, and filter outbound traffic as well. They can keep employees from accessing specific
sites, such as competitors’ sites, sites with pornographic material, or popular news sites. As a
future manager, if you have particular sites with which you do not want your employees to com-
municate, you can ask your IS department to enforce that limit via the firewall.
Personal
Computer 1
Internal Perimeter
Firewall Firewall
Personal
Computer 2
Personal
Computer 3
Mail Web
Personal Server Server Internet
Computer 4 Server Network
Figure 10-11
Use of Multiple Firewalls Local Area Network