Page 32 - ASCCS V8.1 3v02a_delegate version_Neat
P. 32
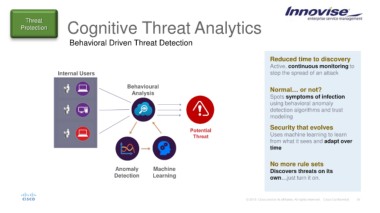
Threat Cognitive Threat Analytics
Protection
Behavioral Driven Threat Detection
Internal Users Reduced time to discovery
Behavioural Active, continuous monitoring to
Analysis stop the spread of an attack
Normal… or not?
Spots symptoms of infection
using behavioral anomaly
detection algorithms and trust
modeling
Security that evolves
Uses machine learning to learn
from what it sees and adapt over
time
Anomaly Machine No more rule sets
Detection Learning
Discovers threats on its
own…just turn it on.