Page 67 - ASCCS V8.1 3v02a_delegate version_Neat
P. 67
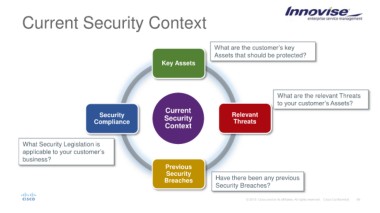
Current Security Context
What are the customer’s key
Assets that should be protected?
Key Assets
What are the relevant Threats
to your customer’s Assets?
Security Current Relevant
Compliance Security Threats
Context
What Security Legislation is
applicable to your customer’s
business?
Previous Have there been any previous
Security Security Breaches?
Breaches