Page 23 - Venafi-eBook-SSH-1709
P. 23
Are your auditors
asking the right
Auditing Practices
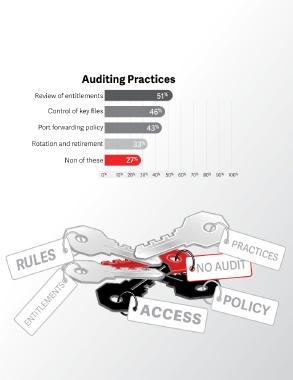
questions about SSH? Review of entitlements 51 %
Control of key files 46 %
An internal or external audit of SSH management
practices can show you how vulnerable you are to SSH Port forwarding policy 43 %
key theft and misuse—but only if audits are regular
and comprehensive. Many executives rely on auditors Rotation and retirement 33 %
to review security controls for their mission critical Non of these 27 %
processes, but most auditors fail to review SSH. Only
half of organizations reported their auditors conduct 0 % 10 % 20 % 30 % 40 % 50 % 60 % 70 % 80 % 90 % 100 %
regular reviews of SSH entitlements and over a
quarter said they don’t audit any of the best practices
surveyed.
The security and integrity of your SSH infrastructure is
critical to protecting your organization’s systems and
data. However, if you’re like most organizations, you
may not have auditor oversight for this critical security PRACTICES
infrastructure. And, even if you do, what would happen RULES
if your audit findings required remediation or other NO AUDIT
action? Are you prepared to act quickly?
Over a quarter do not apply any of the ENTITLEMENTS ACCESS POLICY
auditor best practices surveyed .
22 23