Page 70 - Walter B. Gibson "Knots And How To Tie Them"
P. 70
76
fig. 1
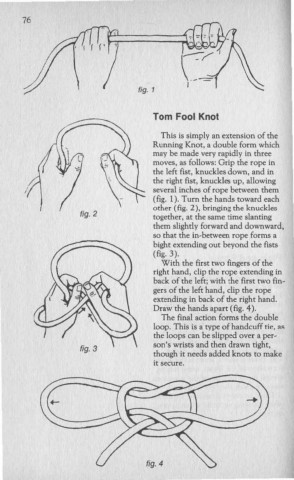
Tom Fool Knot
This is simply an extension of the
Running Knot, a double form which
may be made very rapidly in three
moves, as follows: Grip me rope in
the left fist, knuckles down, and in
the right fist, knuckles up. allowing
several inches of rope between them
(fig. 1). Turn the hands toward each
other (fig. 2), bringing the knuckles
fig. 2 together, at the same time slanting
them slightly forward and downward,
so that the in~between rope forms a
bight extending out beyond the fists
(fig. 3).
With the first two fingers of the
right hand, dip the rope extending in
hack of the left; with the first two fin~
gers of the left hand, dip the rope
extending in back of the right hand.
Draw the hands apart (fig. 4).
The final action forms the double
loop. This is a type of handcuff tie, ~.C;
the loops can be slipped over a per~
son's wrists and then drawn tight,
though it needs added knots to make
it secure.
fig. 4