Page 103 - Hands-On Bug Hunting for Penetration Testers
P. 103
SQL, Code Injection, and Scanners Chapter 5
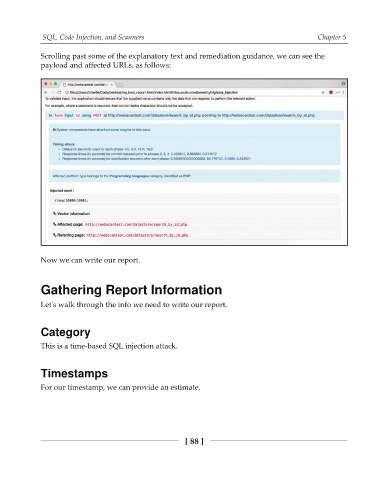
Scrolling past some of the explanatory text and remediation guidance, we can see the
payload and affected URLs, as follows:
Now we can write our report.
Gathering Report Information
Let's walk through the info we need to write our report.
Category
This is a time-based SQL injection attack.
Timestamps
For our timestamp, we can provide an estimate.
[ 88 ]