Page 138 - Hands-On Bug Hunting for Penetration Testers
P. 138
Detecting XML External Entities Chapter 7
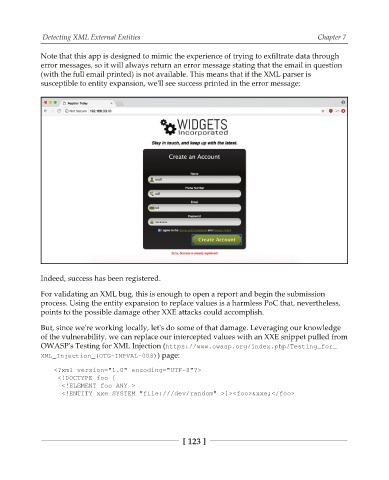
Note that this app is designed to mimic the experience of trying to exfiltrate data through
error messages, so it will always return an error message stating that the email in question
(with the full email printed) is not available. This means that if the XML parser is
susceptible to entity expansion, we'll see success printed in the error message:
Indeed, success has been registered.
For validating an XML bug, this is enough to open a report and begin the submission
process. Using the entity expansion to replace values is a harmless PoC that, nevertheless,
points to the possible damage other XXE attacks could accomplish.
But, since we're working locally, let's do some of that damage. Leveraging our knowledge
of the vulnerability, we can replace our intercepted values with an XXE snippet pulled from
OWASP's Testing for XML Injection (IUUQT XXX PXBTQ PSH JOEFY QIQ 5FTUJOH@GPS@
9.-@*OKFDUJPO@ 05( */17"- ) page:
YNM WFSTJPO FODPEJOH 65'
%0$5:1& GPP <
&-&.&/5 GPP "/:
&/5*5: YYF 4:45&. GJMF EFW SBOEPN > GPP YYF GPP
[ 123 ]