Page 92 - Hands-On Bug Hunting for Penetration Testers
P. 92
SQL, Code Injection, and Scanners Chapter 5
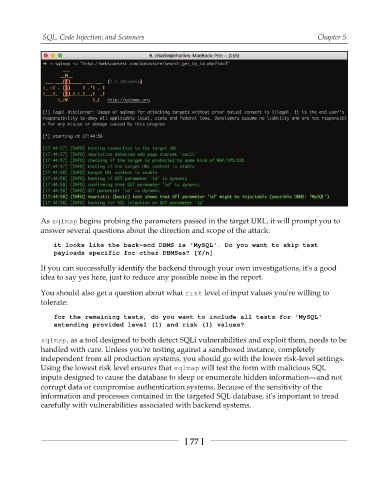
As TRMNBQ begins probing the parameters passed in the target URL, it will prompt you to
answer several questions about the direction and scope of the attack:
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test
payloads specific for other DBMSes? [Y/n]
If you can successfully identify the backend through your own investigations, it's a good
idea to say yes here, just to reduce any possible noise in the report.
You should also get a question about what SJTL level of input values you're willing to
tolerate:
for the remaining tests, do you want to include all tests for 'MySQL'
extending provided level (1) and risk (1) values?
TRMNBQ, as a tool designed to both detect SQLi vulnerabilities and exploit them, needs to be
handled with care. Unless you're testing against a sandboxed instance, completely
independent from all production systems, you should go with the lower risk-level settings.
Using the lowest risk level ensures that TRMNBQ will test the form with malicious SQL
inputs designed to cause the database to sleep or enumerate hidden informationband not
corrupt data or compromise authentication systems. Because of the sensitivity of the
information and processes contained in the targeted SQL database, it's important to tread
carefully with vulnerabilities associated with backend systems.
[ 77 ]