Page 160 - StudyBook.pdf
P. 160
144 Chapter 3 • Communication Security: Remote Access and Messaging
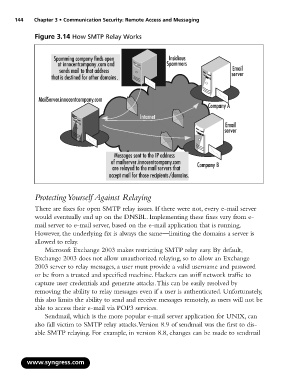
Figure 3.14 How SMTP Relay Works
Spamming company finds open Insidious
at innocentcompany.com and Spammers
Email
sends mail to that address server
that is destined for other domains.
MailServer.innocentcompany.com
Company A
Internet
Email
server
Messages sent to the IP address
of mailserver.innocentcompany.com Company B
are relayed to the mail servers that
accept mail for those recipients/domains.
Protecting Yourself Against Relaying
There are fixes for open SMTP relay issues. If there were not, every e-mail server
would eventually end up on the DNSBL. Implementing these fixes vary from e-
mail server to e-mail server, based on the e-mail application that is running.
However, the underlying fix is always the same—limiting the domains a server is
allowed to relay.
Microsoft Exchange 2003 makes restricting SMTP relay easy. By default,
Exchange 2003 does not allow unauthorized relaying, so to allow an Exchange
2003 server to relay messages, a user must provide a valid username and password
or be from a trusted and specified machine. Hackers can sniff network traffic to
capture user credentials and generate attacks.This can be easily resolved by
removing the ability to relay messages even if a user is authenticated. Unfortunately,
this also limits the ability to send and receive messages remotely, as users will not be
able to access their e-mail via POP3 services.
Sendmail, which is the more popular e-mail server application for UNIX, can
also fall victim to SMTP relay attacks.Version 8.9 of sendmail was the first to dis-
able SMTP relaying. For example, in version 8.8, changes can be made to sendmail
www.syngress.com