Page 169 - StudyBook.pdf
P. 169
Communication Security: Remote Access and Messaging • Chapter 3 153
partner organization.They often address the reality of Internet security threats
within their e-mails!
It is what happens next that should alert the unsavvy user.A phishing e-mail
often has a link to a site. Either within the e-mail or at the site, the victim is asked
to simply provide two or three pieces of information to “update” their files, secu-
rity setting, and so forth. Often, there is the indication that non-compliance will
result in a loss of service to the individual (e.g. their ATM card will no longer
work).The site, while designed very professionally and modestly, is simply an entry
point for personal data that is sent all around the globe for the purposes of identity
theft and fraud.
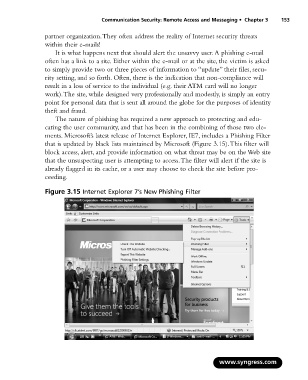
The nature of phishing has required a new approach to protecting and edu-
cating the user community, and that has been in the combining of those two ele-
ments. Microsoft’s latest release of Internet Explorer, IE7, includes a Phishing Filter
that is updated by black lists maintained by Microsoft (Figure 3.15).This filter will
block access, alert, and provide information on what threat may be on the Web site
that the unsuspecting user is attempting to access.The filter will alert if the site is
already flagged in its cache, or a user may choose to check the site before pro-
ceeding.
Figure 3.15 Internet Explorer 7’s New Phishing Filter
www.syngress.com