Page 235 - StudyBook.pdf
P. 235
Communication Security: Wireless • Chapter 4 219
Even if the network administrator has configured his equipment in such a way
as to hide this information, there are tools available that can determine this infor-
mation. Utilizing any of the mentioned network sniffing tools, an attacker can
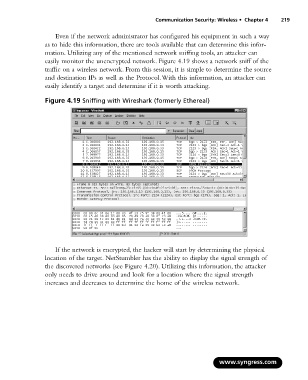
easily monitor the unencrypted network. Figure 4.19 shows a network sniff of the
traffic on a wireless network. From this session, it is simple to determine the source
and destination IPs as well as the Protocol.With this information, an attacker can
easily identify a target and determine if it is worth attacking.
Figure 4.19 Sniffing with Wireshark (formerly Ethereal)
If the network is encrypted, the hacker will start by determining the physical
location of the target. NetStumbler has the ability to display the signal strength of
the discovered networks (see Figure 4.20). Utilizing this information, the attacker
only needs to drive around and look for a location where the signal strength
increases and decreases to determine the home of the wireless network.
www.syngress.com