Page 294 - StudyBook.pdf
P. 294
278 Chapter 5 • Communication Security: Web Based Services
SSL is made up of two protocols, the SSL record protocol and the SSL handshake
protocol. SSL record protocol is used to define the format used to transmit data,
while the SSL handshake protocol uses the record protocol to exchange messages
between the SSL-enabled server and the client when they establish a connection.
Together, these protocols facilitate the definition of the data format that is used in
the transaction and to negotiate the level of encryption and authentication used.
SSL supports a broad range of encryption algorithms, the most common of which
include the RSA key exchange algorithms and the Fortezza algorithms.The
Fortezza encryption suite is used more by U.S. government agencies. SSL 2.0 does
not support the Fortezza algorithms. Its lack of backward compatibility may be
another reason why it is less popular.
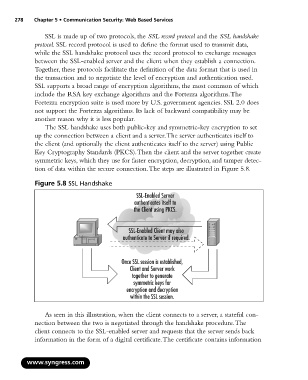
The SSL handshake uses both public-key and symmetric-key encryption to set
up the connection between a client and a server.The server authenticates itself to
the client (and optionally the client authenticates itself to the server) using Public
Key Cryptography Standards (PKCS).Then the client and the server together create
symmetric keys, which they use for faster encryption, decryption, and tamper detec-
tion of data within the secure connection.The steps are illustrated in Figure 5.8.
Figure 5.8 SSL Handshake
SSL-Enabled Server
authenticates itself to
the Client using PKCS.
SSL-Enabled Client may also
authenticate to Server if required.
Once SSL session is established,
Client and Server work
together to generate
symmetric keys for
encryption and decryption
within the SSL session.
As seen in this illustration, when the client connects to a server, a stateful con-
nection between the two is negotiated through the handshake procedure.The
client connects to the SSL-enabled server and requests that the server sends back
information in the form of a digital certificate.The certificate contains information
www.syngress.com