Page 407 - StudyBook.pdf
P. 407
Infrastructure Security: Devices and Media • Chapter 6 391
capable of detecting attacks.They are also more efficient than NIDS because they
only analyze the data from one system rather than the entire network. NIDS, how-
ever, has the ability to detect attacks that may be occurring on multiple systems at
the same time or to catch someone doing a portscan of an entire network.
One of the major benefits of IDSes is that they do not necessarily have to pas-
sively monitor a network. Most IDSes can also perform corrective action when an
attack is identified.This can range from paging the administrator to working with
the firewall to block specific IPs from accessing the network.This is very useful in
blocking attacks and also gathering information about the attackers within the logs.
One of the vulnerabilities of NIDSes is that they can be overloaded. Since they
analyze every packet on the network (or specific subnets), if the network is over-
whelmed with packets the NIDS may not be able to analyze every packet that goes
across. By overloading the NIDS, intruders sometimes avoid detection.As with any
security-related device or application, IDSes should be kept up-to-date with the
most recent updates and signature files from the vendor.
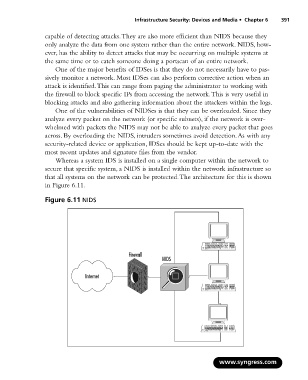
Whereas a system IDS is installed on a single computer within the network to
secure that specific system, a NIDS is installed within the network infrastructure so
that all systems on the network can be protected.The architecture for this is shown
in Figure 6.11.
Figure 6.11 NIDS
Firewall
NIDS
Internet
www.syngress.com