Page 50 - StudyBook.pdf
P. 50
34 Chapter 1 • General Security Concepts: Access Control, Authentication, and Auditing
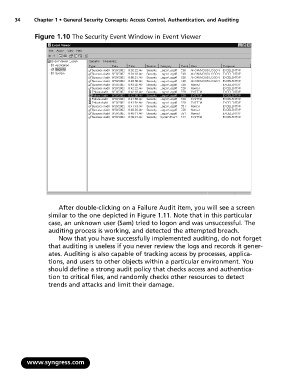
Figure 1.10 The Security Event Window in Event Viewer
After double-clicking on a Failure Audit item, you will see a screen
similar to the one depicted in Figure 1.11. Note that in this particular
case, an unknown user (Sam) tried to logon and was unsuccessful. The
auditing process is working, and detected the attempted breach.
Now that you have successfully implemented auditing, do not forget
that auditing is useless if you never review the logs and records it gener-
ates. Auditing is also capable of tracking access by processes, applica-
tions, and users to other objects within a particular environment. You
should define a strong audit policy that checks access and authentica-
tion to critical files, and randomly checks other resources to detect
trends and attacks and limit their damage.
www.syngress.com