Page 165 - Deception at work all chapters EBook
P. 165
166 Deception at Work
OTHER STUFF
In recent years, many of the large English Law firms put out papers, held lunches, breakfasts,
teas, suppers, soirées, love-ins, workshops and clinics on the Human Rights Act 1998, RIPA
and other worrisome legislation. It is flavour of the year. The result has been to spread panic
and dismay among the great unwashed in investigative communities and to deter victims of
fraud from retaining them, unless under the umbrella of the law firm concerned. This is clever
marketing by the lawyers, and who can blame them?
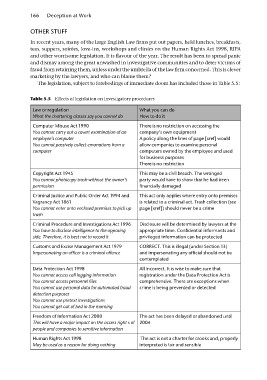
The legislation, subject to forebodings of immediate doom has included those in Table 5.5:
Table 5.5 Effects of legislation on investigatory procedures
Law or regulation What you can do
What the chattering classes say you cannot do How to do it
Computer Misuse Act 1990 There is no restriction on accessing the
You cannot carry out a covert examination of an company’s own equipment
employee’s computer A policy along the lines of page [xref] would
You cannot passively collect emanations from a allow companies to examine personal
computer computers owned by the employee and used
for business purposes
There is no restriction
Copyright Act 1945 This may be a civil breach. The wronged
You cannot photocopy trash without the owner’s party would have to show that he had been
permission financially damaged
Criminal Justice and Public Order Act 1994 and This act only applies where entry onto premises
Vagrancy Act 1861 is related to a criminal act. Trash collection (see
You cannot enter onto enclosed premises to pick up page [xref]) should never be a crime
trash
Criminal Procedure and Investigations Act 1996 Disclosure will be determined by lawyers at the
You have to disclose intelligence to the opposing appropriate time. Confidential informants and
side. Therefore, it is best not to record it privileged information can be protected
Customs and Excise Management Act 1979 CORRECT. This is illegal (under Section 13)
Impersonating an officer is a criminal offence and impersonating any official should not be
contemplated
Data Protection Act 1998 All incorrect. It is wise to make sure that
You cannot access call logging information registration under the Data Protection Act is
You cannot access personnel files comprehensive. There are exceptions when
You cannot use personal data for automated fraud crime is being prevented or detected
detection purposes
You cannot use pretext investigations
You cannot get out of bed in the morning
Freedom of Information Act 2000 The act has been delayed or abandoned until
This will have a major impact on the access right s of 2004
people and companies to sensitive information
Human Rights Act 1998 The act is not a charter for crooks and, properly
May be used as a reason for doing nothing interpreted is fair and sensible