Page 35 - FNSV_Catalog_01_211213
P. 35
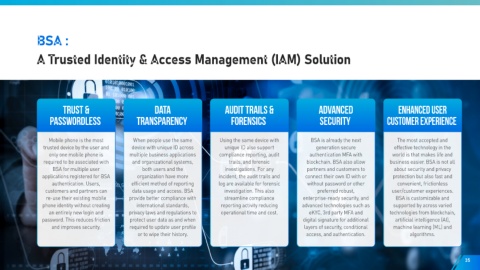
BSA :
A Trusted Identity & Access Management (IAM) Solution
Trust & Data Audit Trails & Advanced Enhanced User
Passwordless Transparency Forensics Security Customer Experience
Mobile phone is the most When people use the same Using the same device with BSA is already the next The most accepted and
trusted device by the user and device with unique ID across unique ID also support generation secure effective technology in the
only one mobile phone is multiple business applications compliance reporting, audit authentication MFA with world is that makes life and
required to be associated with and organizational systems, trails, and forensic blockchain. BSA also allow business easier. BSA is not all
BSA for multiple user both users and the investigations. For any partners and customers to about security and privacy
applications registered for BSA organization have more incident, the audit trails and connect their own ID with or protection but also fast and
authentication. Users, efficient method of reporting log are available for forensic without password or other convenient, frictionless
customers and partners can data usage and access. BSA investigation. This also preferred robust, user/customer experiences.
re-use their existing mobile provide better compliance with streamline compliance enterprise-ready security, and BSA is customizable and
phone identity without creating international standards, reporting activity reducing advanced technologies such as supported by across varied
an entirely new login and privacy laws and regulations to operational time and cost. eKYC, 3rd party MFA and technologies from blockchain,
password. This reduces friction protect user data as and when digital signature for additional artificial intelligence (AI),
and improves security. required to update user profile layers of security, conditional machine learning (ML) and
or to wipe their history. access, and authentication. algorithms.
35