Page 13 - Internal Auditor M.E. (English) - June 2018
P. 13
information Security
• Sign-off of user acceptance policy, including all information Auditing ISR version 2
security policies.
ISR is a regulatory document which defines information
These steps are a prelude to the requirements to involve security law in the UAEs. This means planning ISR auditing
management and enforcement of policies and procedures for needs to consider:
all domains. Hence, ISR version 2 governance requirements
provide that Director-General or CEO, together with • Law and regulations (Reference: ISR version 2 Section 11.1
divisional managers or heads, be involved in the ISSC Compliance with Federal and Local Government Legal
as participants. The idea is to actively involve them in Requirements).
ISR implementation activities. This requires effort in the • Internal DGE policies and procedures.
following spheres.
• Other information security standards implemented.
These additional considerations add a burden on audit
Booking time Defining Keeping Ensuring Documenting planning, with the auditor needing to cross-match these
of Director- specific the ISSC informed meeting results inputs to develop an audit plan incorporating regulatory
General and items in members and timely and decisions
department the ISSC updated on decision- to make sure requirements.
heads on a agenda issues to be making actions are
regular basis to be discussed occurs implemented in ISR audit in action
discussed at ISSC a timely way
meetings A specific approach to ISR audit planning is required to
ensure the audit does not miss any vital part of related
Governance legislation. The audit approach has to factor in specifics of the
DGE being audited. Audit clients tend to be critical of auditor
Good governance requires performance measures (KPIs) to approach and lack of subject matter knowledge. A cyclical
be identified that link desired outputs and outcomes. For audit approach such as shown in the following diagram can be
example, Directors-General may not know intimately capacity useful to ensure focus on the audit objectives.
management, but if a KPI figure is 80% and this is exceeded,
then early warning is achieved. Allocate tasks Build asset
as per action register with
plan and
the active
Another change is Chief Information Security Officer (CISO) identify points involvement
reporting to the Director-General or ISSC, which represents to proceed of information
a change from ISR version 1 to ISR version 2. This is aimed for next audit system users
at providing a CISO with direct access to decision-making cycle
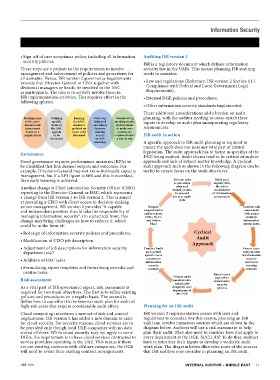
senior management. ISR version 2 provides “A capable Prepare Conduct risk
and independent position should take the responsibility of comprehensive assessment
with actual
audits reports
managing information security”. On a practical front, this (ISSC, IS, IT, examples
change may bring challenges on how to enforce it, which and Action information
could be in the form of: Plan) system users
• Redesign of information security policies and procedures. Cyclical
Audit
• Modification of CISO job description. Approach
• Adjustment of job descriptions for information security Conduct Audit Ensure users
department staff and capture participation
specific users in information
security
concerns in
• Addition of ISSC tasks. information awareness
• Formulating report templates and formalizing periodic and security training
controls
sessions
routine tasks.
Prepare audit Ensure users
sign off on
Risk assessment questionnaire information
specifically security
As a vital part of ISR governance aspect, risk assessment is design for each policies
required for two main objectives. The first is to refine existing department of
the DGE
policies and procedures on a regular basis. The second is
define how to cap effort in the internal audit plan for audit of
high-risk areas that require considerable audit effort. Planning for an ISR audit
Cloud computing introduces a new set of risk and control ISR version 2 implementation comes with laws and
implications. ISR version 2 has added a new domain to cater regulations to consider. For this reason, planning an ISR
for cloud security. For security reasons, cloud services are to audit can involve numerous sources which are shown in the
be provided only though local UAE companies with no data diagram below. Auditors will use a risk assessment to help
stored offshore. While cloud security may not apply to some plan their audit. They also need to consider laws that apply to
DGEs, the requirement is to have cloud services contracted to every department at the DGE. SUCH AS? To do that, auditors
service providers operating in the UAE. This means if there have to prioritize their inputs to develop a workable audit
are pre-existing contracts with offshore companies, the DGE work plan. The diagram below illustrates some of the sources
will need to revise their existing contract arrangements. that ISR auditors may consider in planning an ISR audit.
JUNE 2018 INTERNAL AUDITOR - MIDDLE EAST 11