Page 374 - ITGC_Audit Guides
P. 374
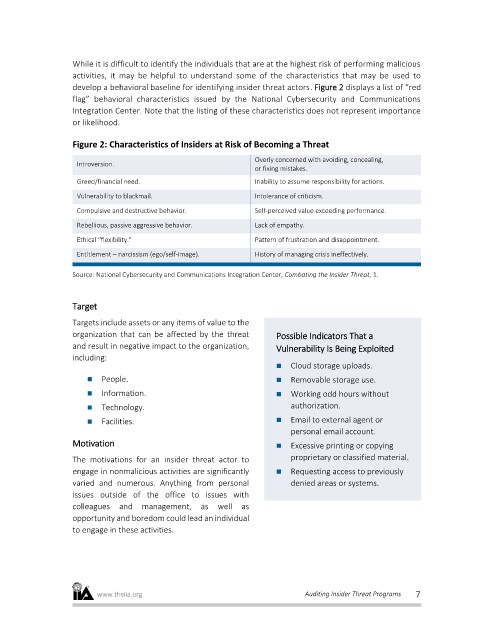
While it is difficult to identify the individuals that are at the highest risk of performing malicious
activities, it may be helpful to understand some of the characteristics that may be used to
develop a behavioral baseline for identifying insider threat actors. Figure 2 displays a list of “red
flag” behavioral characteristics issued by the National Cybersecurity and Communications
Integration Center. Note that the listing of these characteristics does not represent importance
or likelihood.
Figure 2: Characteristics of Insiders at Risk of Becoming a Threat
Overly concerned with avoiding, concealing,
Introversion.
or fixing mistakes.
Greed/financial need. Inability to assume responsibility for actions.
Vulnerability to blackmail. Intolerance of criticism.
Compulsive and destructive behavior. Self-perceived value exceeding performance.
Rebellious, passive aggressive behavior. Lack of empathy.
Ethical “flexibility.” Pattern of frustration and disappointment.
Entitlement – narcissism (ego/self-image). History of managing crisis ineffectively.
Source: National Cybersecurity and Communications Integration Center, Combating the Insider Threat, 1.
Target
Targets include assets or any items of value to the
organization that can be affected by the threat Possible Indicators That a
and result in negative impact to the organization, Vulnerability Is Being Exploited
including:
Cloud storage uploads.
People. Removable storage use.
Information. Working odd hours without
Technology. authorization.
Facilities. Email to external agent or
personal email account.
Motivation Excessive printing or copying
The motivations for an insider threat actor to proprietary or classified material.
engage in nonmalicious activities are significantly Requesting access to previously
varied and numerous. Anything from personal denied areas or systems.
issues outside of the office to issues with
colleagues and management, as well as
opportunity and boredom could lead an individual
to engage in these activities.
www.theiia.org Auditing Insider Threat Programs 7