Page 375 - ITGC_Audit Guides
P. 375
Motivations for malicious attacks may include, but are not limited to:
Financial gain. Revenge.
Fraud. Espionage.
Mischief. Theft.
Malice. Association with criminals.
Negative Impact
The impact of insiders exploiting a vulnerability can be categorized following the Committee of
Sponsoring Organizations of the Treadway Commission (COSO) Enterprise Risk Management
Framework as financial, operational, compliance, and customer. It is common that one attack can
result in more than one impact category; for example, sabotage of critical information systems can
result in financial (cost to restore systems), operational (loss of productivity), and customer (poor
service during outage) impacts.
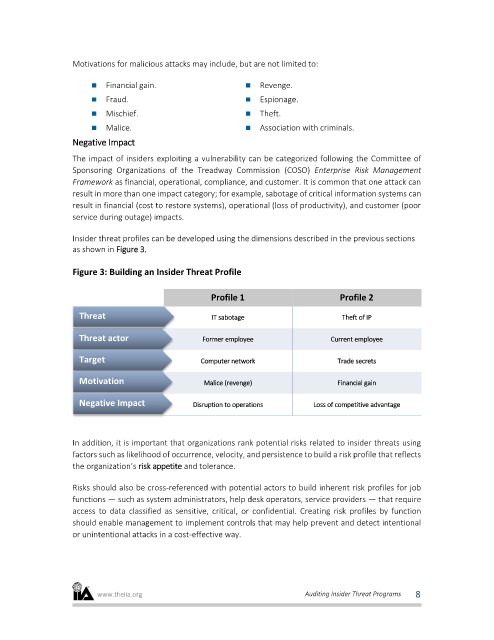
Insider threat profiles can be developed using the dimensions described in the previous sections
as shown in Figure 3.
Figure 3: Building an Insider Threat Profile
Profile 1 Profile 2
Threat IT sabotage Theft of IP
Threat actor Former employee Current employee
Target Computer network Trade secrets
Motivation Malice (revenge) Financial gain
Negative Impact Disruption to operations Loss of competitive advantage
In addition, it is important that organizations rank potential risks related to insider threats using
factors such as likelihood of occurrence, velocity, and persistence to build a risk profile that reflects
the organization’s risk appetite and tolerance.
Risks should also be cross-referenced with potential actors to build inherent risk profiles for job
functions — such as system administrators, help desk operators, service providers — that require
access to data classified as sensitive, critical, or confidential. Creating risk profiles by function
should enable management to implement controls that may help prevent and detect intentional
or unintentional attacks in a cost-effective way.
www.theiia.org Auditing Insider Threat Programs 8