Page 39 - ITGC_Audit Guides
P. 39
WEP (Wired Equivalent Privacy) – an outdated security protocol that offers basic
encryption. This protocol is typically used because it may be the only option for older
infrastructures. From a security standpoint, given sufficient traffic and even marginal
computing power on a laptop or mobile device, WEP is easily penetrated and was
superseded by the WPA protocol by the Wi-Fi Alliance in 2003.
WPA (Wi-Fi Protected Access) – replaced WEP as a more secure security protocol for
wireless networks. Like WEP, WPA should only be used if required by older infrastructure
because it is vulnerable and provides less encryption than its successors.
WPA2 (Wi-Fi Protected Access 2) – security protocol currently required on all devices
considered Wi-Fi CERTIFIED by the Wi-Fi Alliance, providing stronger encryption algorithms
than predecessors. It provides a degree of security from unauthorized access.
WPA3 (Wi-Fi Protected Access 3) – provides individual data encryption, secures some
“internet of things” (IoT) devices, protects against brute force (trial and error approach),
dictionary attacks (using dictionary words to guess passwords), and offers the highest current
level of encryption.
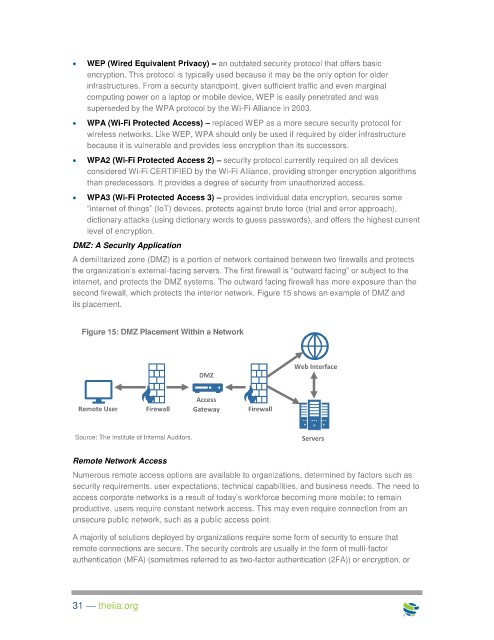
DMZ: A Security Application
A demilitarized zone (DMZ) is a portion of network contained between two firewalls and protects
the organization’s external-facing servers. The first firewall is “outward facing” or subject to the
internet, and protects the DMZ systems. The outward facing firewall has more exposure than the
second firewall, which protects the interior network. Figure 15 shows an example of DMZ and
its placement.
Figure 15: DMZ Placement Within a Network
Web Interface
DMZ
Access
Remote User Firewall Gateway Firewall
Source: The Institute of Internal Auditors. Servers
Remote Network Access
Numerous remote access options are available to organizations, determined by factors such as
security requirements, user expectations, technical capabilities, and business needs. The need to
access corporate networks is a result of today’s workforce becoming more mobile; to remain
productive, users require constant network access. This may even require connection from an
unsecure public network, such as a public access point.
A majority of solutions deployed by organizations require some form of security to ensure that
remote connections are secure. The security controls are usually in the form of multi-factor
authentication (MFA) (sometimes referred to as two-factor authentication (2FA)) or encryption, or
31 — theiia.org