Page 592 - ITGC_Audit Guides
P. 592
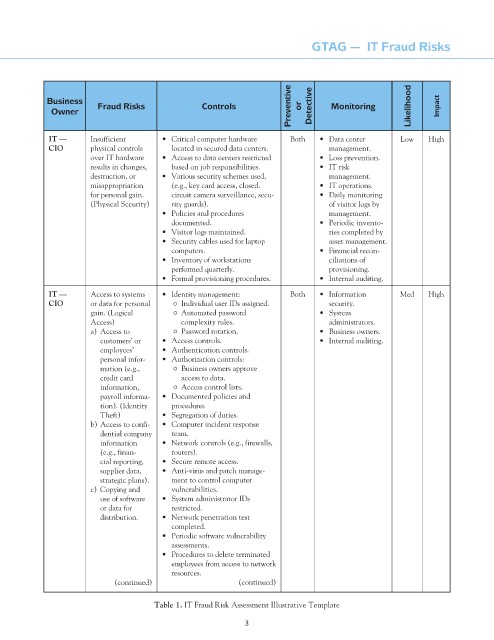
GTAG — IT Fraud Risks
Preventive or Detective Monitoring Likelihood Impact
Business
Fraud Risks
Controls
Owner
it — Insufficient • Critical computer hardware Both • Data center Low High
cio physical controls located in secured data centers. management.
over IT hardware • Access to data centers restricted • Loss prevention.
results in changes, based on job responsibilities. • IT risk
destruction, or • Various security schemes used, management.
misappropriation (e.g., key card access, closed. • IT operations.
for personal gain. circuit camera surveillance, secu- • Daily monitoring
(Physical Security) rity guards). of visitor logs by
• Policies and procedures management.
documented. • Periodic invento-
• Visitor logs maintained. ries completed by
• Security cables used for laptop asset management.
computers. • Financial recon-
• Inventory of workstations ciliations of
performed quarterly. provisioning.
• Formal provisioning procedures. • Internal auditing.
it — Access to systems • Identity management: Both • Information Med High
cio or data for personal Individual user IDs assigned. security.
gain. (Logical Automated password • System
Access) complexity rules. administrators.
a) Access to Password rotation. • Business owners.
customers’ or • Access controls. • Internal auditing.
employees’ • Authentication controls.
personal infor- • Authorization controls:
mation (e.g., Business owners approve
credit card access to data.
information, Access control lists.
payroll informa- • Documented policies and
tion). (Identity procedures
Theft) • Segregation of duties.
b) Access to confi- • Computer incident response
dential company team.
information • Network controls (e.g., firewalls,
(e.g., finan- routers).
cial reporting, • Secure remote access.
supplier data, • Anti-virus and patch manage-
strategic plans). ment to control computer
c) Copying and vulnerabilities.
use of software • System administrator IDs
or data for restricted.
distribution. • Network penetration test
completed.
• Periodic software vulnerability
assessments.
• Procedures to delete terminated
employees from access to network
resources.
(continued) (continued)
table 1. IT Fraud Risk Assessment Illustrative Template
3