Page 593 - ITGC_Audit Guides
P. 593
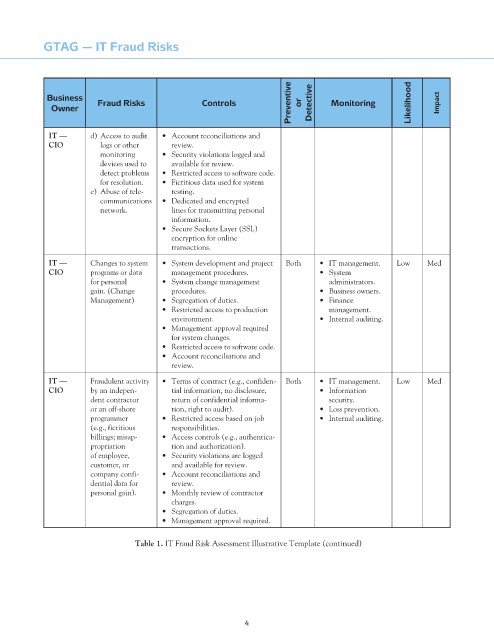
GTAG — IT Fraud Risks
Preventive or Detective Monitoring Likelihood Impact
Business
Controls
Fraud Risks
Owner
it — d) Access to audit • Account reconciliations and
cio logs or other review.
monitoring • Security violations logged and
devices used to available for review.
detect problems • Restricted access to software code.
for resolution. • Fictitious data used for system
e) Abuse of tele- testing.
communications • Dedicated and encrypted
network. lines for transmitting personal
information.
• Secure Sockets Layer (SSL)
encryption for online
transactions.
it — Changes to system • System development and project Both • IT management. Low Med
cio programs or data management procedures. • System
for personal • System change management administrators.
gain. (Change procedures. • Business owners.
Management) • Segregation of duties. • Finance
• Restricted access to production management.
environment. • Internal auditing.
• Management approval required
for system changes.
• Restricted access to software code.
• Account reconciliations and
review.
it — Fraudulent activity • Terms of contract (e.g., confiden- Both • IT management. Low Med
cio by an indepen- tial information, no disclosure, • Information
dent contractor return of confidential informa- security.
or an off-shore tion, right to audit). • Loss prevention.
programmer • Restricted access based on job • Internal auditing.
(e.g., fictitious responsibilities.
billings; misap- • Access controls (e.g., authentica-
propriation tion and authorization).
of employee, • Security violations are logged
customer, or and available for review.
company confi- • Account reconciliations and
dential data for review.
personal gain). • Monthly review of contractor
charges.
• Segregation of duties.
• Management approval required.
table 1. IT Fraud Risk Assessment Illustrative Template (continued)
4