Page 8 - Reduce security blind spots and paralyze ransomware
P. 8
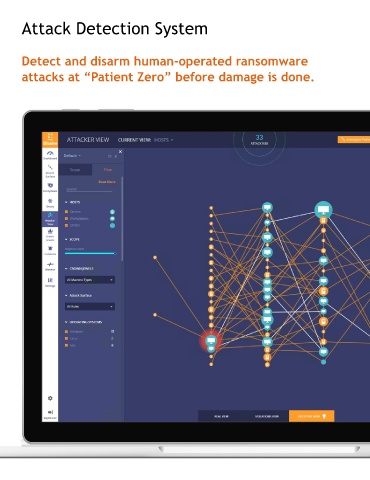
Attack Detection System Agentless, intelligence-driven technology
Illusive Attack Detection System (ADS) is an agentless, intelligence-driven technology that is easily
deployed without significant involvement from IT teams, saving your business precious time and
Detect and disarm human-operated ransomware resources. ADS reduces noise in the security operations center and remains unobtrusive to security
attacks at “Patient Zero” before damage is done. team users, yet it has the capacity to scale to support organizations of any size.
Once the Azure AD environment is clean, the
Illusive Attack Detection System effortlessly
creates a dense web of deceptions on every
endpoint that mimic the real data, credentials,
and connections ransomware attackers exploit.
Confronted with a distorted view of reality,
it becomes extremely difficult for attackers
to choose a real path forward, fooling them
into revealing their malicious presence in the
environment. With the defender now in the
driver’s seat, incident response teams have an
opportunity to stop ransomware attackers before
they can reach critical business assets and launch
their encryption payloads.