Page 16 - Information_Security_Program
P. 16
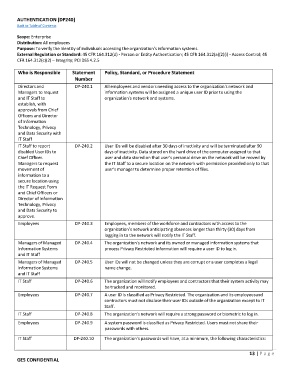
AUTHENTICATION [DP240]
Back to Table of Contents
Scope: Enterprise
Distribution: All employees
Purpose: To verify the identity of individuals accessing the organization’s information systems.
External Regulation or Standard: 45 CFR 164.312(d) ‐ Person or Entity Authentication; 45 CFR 164.312(a)(2)(i) ‐ Access Control; 45
CFR 164.312(c)(2) – Integrity; PCI DSS 4.2.5
Who is Responsible Statement Policy, Standard, or Procedure Statement
Number
Directors and DP‐240.1 All employees and vendors needing access to the organization's network and
Managers to request information systems will be assigned a unique user ID prior to using the
and IT Staff to organization's network and systems.
establish, with
approvals from Chief
Officers and Director
of Information
Technology, Privacy
and Data Security with
IT Staff
IT Staff to report DP‐240.2 User IDs will be disabled after 30 days of inactivity and will be terminated after 90
disabled User IDs to days of inactivity. Data stored on the hard drive of the computer assigned to that
Chief Officer. user and data stored on that user’s personal drive on the network will be moved by
Managers to request the IT Staff to a secure location on the network with permission provided only to that
movement of user’s manager to determine proper retention of files.
information to a
secure location using
the IT Request Form
and Chief Officers or
Director of Information
Technology, Privacy
and Data Security to
approve.
Employees DP‐240.3 Employees, members of the workforce and contractors with access to the
organization’s network anticipating absences longer than thirty (30) days from
logging in to the network will notify the IT Staff.
Managers of Managed DP‐240.4 The organization's network and its owned or managed information systems that
Information Systems process Privacy Restricted information will require a user ID to log in.
and IT Staff
Managers of Managed DP‐240.5 User IDs will not be changed unless they are corrupt or a user completes a legal
Information Systems name change.
and IT Staff
IT Staff DP‐240.6 The organization will notify employees and contractors that their system activity may
be tracked and monitored.
Employees DP‐240.7 A user ID is classified as Privacy Restricted. The organization and its employeesand
contractors must not disclose their user IDs outside of the organization except to IT
Staff.
IT Staff DP‐240.8 The organization's network will require a strong password or biometric to log in.
Employees DP‐240.9 A system password is classified as Privacy Restricted. Users must not share their
passwords with others.
IT Staff DP‐240.10 The organization's passwords will have, at a minimum, the following characteristics:
13 | Page
GES CONFIDENTIAL