Page 17 - Information_Security_Program
P. 17
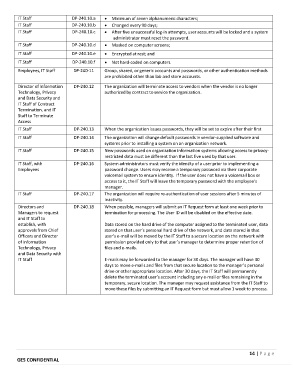
IT Staff DP‐240.10.a Minimum of seven alphanumeric characters;
IT Staff DP‐240.10.b Changed every 90 days;
IT Staff DP‐240.10.c After five unsuccessful log‐in attempts, user accounts will be locked and a system
administrator must reset the password.
IT Staff DP‐240.10.d Masked on computer screens;
IT Staff DP‐240.10.e Encrypted at rest; and
IT Staff DP‐240.10.f Not hard‐coded on computers.
Employees, IT Staff DP‐240‐11 Group, shared, or generic accounts and passwords, or other authentication methods
are prohibited other than lab and store accounts.
Director of Information DP‐240.12 The organization will terminate access to vendors when the vendor is no longer
Technology, Privacy authorized by contract to service the organization.
and Data Security and
IT Staff of Contract
Termination, and IT
Staff to Terminate
Access
IT Staff DP‐240.13 When the organization issues passwords, they will be set to expire after their first
use
IT Staff DP‐240.14 The organization will change default passwords in vendor‐supplied software and
systems prior to installing a system on an organization network.
IT Staff DP‐240.15 New passwords used on organization information systems allowing access to privacy‐
restricted data must be different than the last five used by that user.
IT Staff, with DP‐240.16 System administrators must verify the identity of a user prior to implementing a
Employees password change. Users may receive a temporary password via their corporate
voicemail system to ensure identity. If the user does not have a voicemail box or
access to it, the IT Staff will leave the temporary password with the employee’s
manager.
IT Staff DP‐240.17 The organization will require re‐authentication of user sessions after 5 minutes of
inactivity.
Directors and DP‐240.18 When possible, managers will submit an IT Request form at least one week prior to
Managers to request termination for processing. The User ID will be disabled on the effective date.
and IT Staff to
establish, with Data stored on the hard drive of the computer assigned to the terminated user, data
approvals from Chief stored on that user’s personal hard drive of the network, and data stored in that
Officers and Director user’s e‐mail will be moved by the IT Staff to a secure location on the network with
of Information permission provided only to that user’s manager to determine proper retention of
Technology, Privacy files and e‐mails.
and Data Security with
IT Staff E‐mails may be forwarded to the manager for 30 days. The manager will have 30
days to move e‐mails and files from that secure location to the manager’s personal
drive or other appropriate location. After 30 days, the IT Staff will permanently
delete the terminated user’s account including any e‐mail or files remaining in the
temporary, secure location. The manager may request assistance from the IT Staff to
move these files by submitting an IT Request form but must allow 1 week to process.
14 | Page
GES CONFIDENTIAL