Page 23 - Information_Security_Program
P. 23
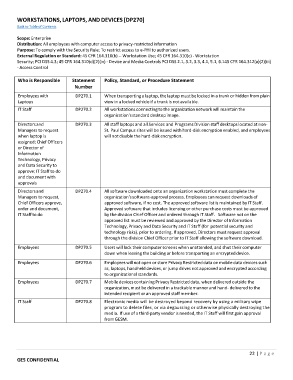
WORKSTATIONS, LAPTOPS, AND DEVICES [DP270]
Back to Table of Contents
Scope: Enterprise
Distribution: All employees with computer access to privacy‐restricted information
Purpose: To comply with the Security Rule; To restrict access to e‐PHI to authorized users.
External Regulation or Standard: 45 CFR 164.310(b) ‐‐ Workstation Use; 45 CFR 164.310(c) ‐ Workstation
Security; PCI DSS 4.3; 45 CFR 164.310(d)(2)(iv) ‐ Device and Media Controls PCI DSS 2.1, 3.2, 3.3, 4.1, 5.1, 6.145 CFR 164.312(a)(2)(iii)
‐ Access Control
Who is Responsible Statement Policy, Standard, or Procedure Statement
Number
Employees with DP270.1 When transporting a laptop, the laptop must be locked in a trunk or hidden from plain
Laptops view in a locked vehicle if a trunk is not available.
IT Staff DP270.2 All workstationsconnecting to the organizationnetwork will maintain the
organization's standard desktop image.
Directors and DP270.3 All staff laptops and all Services and Programs Division staff desktops located at non‐
Managers to request St. Paul Campus sites will be issued with hard‐disk encryption enabled, and employees
when laptop is will not disable the hard‐disk encryption.
assigned; Chief Officers
or Director of
Information
Technology, Privacy
and Data Security to
approve; IT Staff to do
and document with
approvals
Directors and DP270.4 All software downloaded onto an organizationworkstation must complete the
Managers to request, organization's software‐approval process. Employees can request downloads of
Chief Officers approve, approved software, if no cost. The approved software list is maintained by IT Staff.
order and document, Approved software that includes licensing or other purchase costs must be approved
IT Staff to do by the division Chief Officer and ordered through IT Staff. Software not on the
approved list must be reviewed and approved by the Director of Information
Technology, Privacy and Data Security and IT Staff (for potential security and
technology risks), prior to ordering. If approved, Directors must request approval
through the division Chief Officer prior to IT Staff allowing the software download.
Employees DP270.5 Users will lock their computer screens when unattended, and shut their computer
down when leaving the building or before transporting an encrypted device.
Employees DP270.6 Employees will not open or store Privacy Restricted data on mobile data devices such
as, laptops, handheld devices, or jump drives not approved and encrypted according
to organizational standards.
Employees DP270.7 Mobile devicescontaining PrivacyRestricteddata, when delivered outside the
organization, must be delivered in a trackable manner and hand‐ delivered to the
intended recipient or an approved staff member.
IT Staff DP270.8 Electronic media will be destroyed beyond recovery by using a military wipe
program to delete files, or via degaussing or otherwise physically destroying the
media. If use of a third‐party vendor is needed, the IT Staff will first gain approval
from GESM.
22 | P a g e
GES CONFIDENTIAL