Page 28 - Information_Security_Program
P. 28
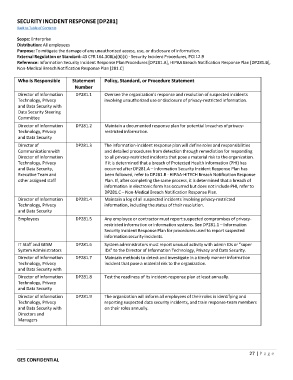
SECURITY INCIDENT RESPONSE [DP281]
Back to Table of Contents
Scope: Enterprise
Distribution: All employees
Purpose: To mitigate the damage of any unauthorized access, use, or disclosure of information.
External Regulation or Standard: 45 CFR 164.308(a)(6)(ii) ‐ Security Incident Procedures, PCI 12.9
Reference: Information Security Incident Response Plan Procedures [DP281.A], HIPAA Breach Notification Response Plan [DP281.B],
Non‐Medical Breach Notification Response Plan [281.C]
Who is Responsible Statement Policy, Standard, or Procedure Statement
Number
Director of Information DP281.1 Oversee the organization's response and resolution of suspected incidents
Technology, Privacy involving unauthorized use or disclosure of privacy‐restricted information.
and Data Security with
Data Security Steering
Committee
Director of Information DP281.2 Maintain a documented response plan for potential breaches of privacy‐
Technology, Privacy restricted information.
and Data Security
Director of DP281.3 The information‐incident response plan will define roles and responsibilities
Communications with and detailed procedures from detection through remediation for responding
Director of Information to all privacy‐restricted incidents that pose a material risk to the organization.
Technology, Privacy If it is determined that a breach of Protected Health Information (PHI) has
and Data Security, occurred after DP281.A – Information Security Incident Response Plan has
Executive Team and been followed, refer to DP281.B ‐ HIPAA‐HITECH Breach Notification Response
other assigned staff Plan. If, after completing the same process, it is determined that a breach of
information in electronic form has occurred but does not include PHI, refer to
DP281.C – Non‐Medical Breach Notification Response Plan.
Director of Information DP281.4 Maintain a log of all suspected incidents involving privacy‐restricted
Technology, Privacy information, including the status of their resolution.
and Data Security
Employees DP281.5 Any employee or contractor must report suspected compromises of privacy‐
restricted information or information systems. See DP281.1 – Information
Security Incident Response Plan for procedures used to report suspected
information security incidents.
IT Staff and GESM DP281.6 System administrators must report unusual activity with admin IDs or "super
System Administrators IDs" to the Director of Information Technology, Privacy and Data Security.
Director of Information DP281.7 Maintain methods to detect and investigate in a timely manner information
Technology, Privacy incident that pose a material risk to the organization.
and Data Security with
Director of Information DP281.8 Test the readiness of its incident‐response plan at least annually.
Technology, Privacy
and Data Security
Director of Information DP281.9 The organization will inform all employees of their roles in identifying and
Technology, Privacy reporting suspected data security incidents, and train response‐team members
and Data Security with on their roles annually.
Directors and
Managers
27 | P a g e
GES CONFIDENTIAL