Page 32 - Information_Security_Program
P. 32
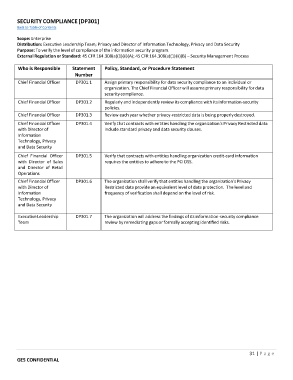
SECURITY COMPLIANCE [DP301]
Back to Table of Contents
Scope: Enterprise
Distribution: Executive Leadership Team; Privacy and Director of Information Technology, Privacy and Data Security
Purpose: To verify the level of compliance of the information security program.
External Regulation or Standard: 45 CFR 164.308(a)(1)(ii)(A); 45 CFR 164.308(a)(1)(ii)(B) – Security Management Process
Who is Responsible Statement Policy, Standard, or Procedure Statement
Number
Chief Financial Officer DP301.1 Assign primary responsibility for data security compliance to an individual or
organization. The Chief Financial Officer will assume primary responsibility for data
security compliance.
Chief Financial Officer DP301.2 Regularly and independently review its compliance with its information‐security
policies.
Chief Financial Officer DP301.3 Review each year whether privacy‐restricted data is being properly destroyed.
Chief Financial Officer DP301.4 Verify that contracts with entities handling the organization's Privacy Restricted data
with Director of include standard privacy and data security clauses.
Information
Technology, Privacy
and Data Security
Chief Financial Officer DP301.5 Verify that contracts with entities handling organization credit‐card information
with Director of Sales requires the entities to adhere to the PCI DSS.
and Director of Retail
Operations
Chief Financial Officer DP301.6 The organization shall verify that entities handling the organization's Privacy
with Director of Restricted data provide an equivalent level of data protection. The level and
Information frequency of verification shall depend on the level of risk.
Technology, Privacy
and Data Security
Executive Leadership DP301.7 The organization will address the findings of its information‐security compliance
Team review by remediating gaps or formally accepting identified risks.
31 | P a g e
GES CONFIDENTIAL