Page 12 - ISCI’2017
P. 12
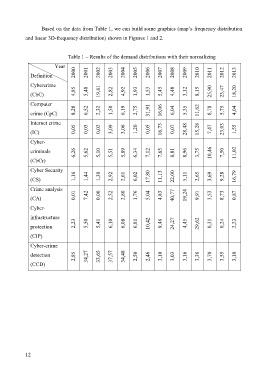
Based on the data from Table 1, we can build some graphics (map’s frequency distribution
and linear 3D-frequency distribution) shown in Figures 1 and 2.
Table 1 – Results of the demand distributions with their normalizing
Year
Definition 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013
Cybercrime
(CbC) 4,85 5,48 19,81 2,82 4,92 1,93 1,53 5,45 4,48 3,12 8,15 25,90 23,47 18,20
Computer
crime (CpC) 8,28 6,52 2,32 1,50 6,19 2,75 31,91 16,06 6,04 5,35 11,62 8,78 5,75 4,04
Internet crime
(IC) 0,05 0,03 0,02 3,09 3,06 1,20 0,05 16,73 0,07 28,48 15,28 7,47 23,03 1,55
Cyber-
criminals 6,26 5,62 5,10 5,51 5,89 6,34 7,12 7,65 8,81 8,96 3,75 10,46 7,50 11,02
(CbCr)
Cyber Security
(CS) 1,16 1,44 1,30 2,92 2,61 6,02 17,80 11,13 22,00 5,11 2,65 3,69 9,28 16,79
Crime analysis
(CA) 0,01 7,42 0,00 2,52 2,80 1,76 5,04 4,83 40,77 19,24 9,91 3,53 8,73 0,87
Cyber-
infrastructure
protection 2,23 5,50 5,41 6,10 6,08 6,81 10,42 9,46 24,27 4,45 29,62 0,31 0,24 2,23
(CIP)
Cyber-crime
detection 2,85 34,27 33,65 37,57 34,48 2,50 2,46 3,10 3,03 3,16 3,36 3,70 3,55 3,10
(CCD)
12