Page 385 - From GMS to LTE
P. 385
VoLTE, VoWifi and Mission Critical Communication 371
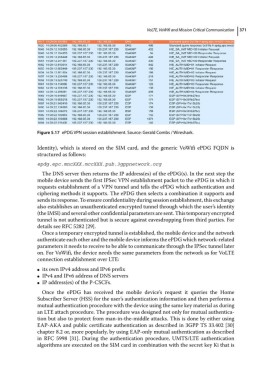
Figure 5.17 ePDG VPN session establishment. Source: Gerald Combs / Wireshark.
Identity), which is stored on the SIM card, and the generic VoWifi ePDG FQDN is
structured as follows:
epdg.epc.mncXXX.mccXXX.pub.3gppnetwork.org
The DNS server then returns the IP address(es) of the ePDG(s). In the next step the
mobile device sends the first IPSec VPN establishment packet to the ePDG in which it
requests establishment of a VPN tunnel and tells the ePDG which authentication and
ciphering methods it supports. The ePDG then selects a combination it supports and
sends its response. To ensure confidentiality during session establishment, this exchange
also establishes an unauthenticated encrypted tunnel through which the user’s identity
(the IMSI) and several other confidential parameters are sent. This temporary encrypted
tunnel is not authenticated but is secure against eavesdropping from third parties. For
details see RFC 5282 [29].
Once a temporary encrypted tunnel is established, the mobile device and the network
authenticate each other and the mobile device informs the ePDG which network‐related
parameters it needs to receive to be able to communicate through the IPSec tunnel later
on. For VoWifi, the device needs the same parameters from the network as for VoLTE
connection establishment over LTE:
its own IPv4 address and IPv6 prefix
●
IPv4 and IPv6 address of DNS servers
●
IP address(es) of the P‐CSCFs.
●
Once the ePDG has received the mobile device’s request it queries the Home
Subscriber Server (HSS) for the user’s authentication information and then performs a
mutual authentication procedure with the device using the same key material as during
an LTE attach procedure. The procedure was designed not only for mutual authentica-
tion but also to protect from man‐in‐the‐middle attacks. This is done by either using
EAP‐AKA and public certificate authentication as described in 3GPP TS 33.402 [30]
chapter 8.2 or, more popularly, by using EAP‐only mutual authentication as described
in RFC 5998 [31]. During the authentication procedure, UMTS/LTE authentication
algorithms are executed on the SIM card in combination with the secret key Ki that is