Page 59 - From GMS to LTE
P. 59
Global System for Mobile Communications (GSM) 45
…
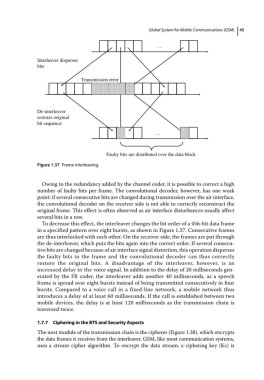
Interleaver disperses
bits
Transmission error
De-interleaver
restores original
bit sequence
…
Faulty bits are distributed over the data block
Figure 1.37 Frame interleaving.
Owing to the redundancy added by the channel coder, it is possible to correct a high
number of faulty bits per frame. The convolutional decoder, however, has one weak
point: if several consecutive bits are changed during transmission over the air interface,
the convolutional decoder on the receiver side is not able to correctly reconstruct the
original frame. This effect is often observed as air interface disturbances usually affect
several bits in a row.
To decrease this effect, the interleaver changes the bit order of a 456‐bit data frame
in a specified pattern over eight bursts, as shown in Figure 1.37. Consecutive frames
are thus interlocked with each other. On the receiver side, the frames are put through
the de‐interleaver, which puts the bits again into the correct order. If several consecu-
tive bits are changed because of air interface signal distortion, this operation disperses
the faulty bits in the frame and the convolutional decoder can thus correctly
restore the original bits. A disadvantage of the interleaver, however, is an
increased delay in the voice signal. In addition to the delay of 20 milliseconds gen-
erated by the FR coder, the interleaver adds another 40 milliseconds, as a speech
frame is spread over eight bursts instead of being transmitted consecutively in four
bursts. Compared to a voice call in a fixed‐line network, a mobile network thus
introduces a delay of at least 60 milliseconds. If the call is established between two
mobile devices, the delay is at least 120 milliseconds as the transmission chain is
traversed twice.
1.7.7 Ciphering in the BTS and Security Aspects
The next module of the transmission chain is the cipherer (Figure 1.38), which encrypts
the data frames it receives from the interleaver. GSM, like most communication systems,
uses a stream cipher algorithm. To encrypt the data stream, a ciphering key (Kc) is