Page 441 - Handbook of Modern Telecommunications
P. 441
3-232 CRC Handbook of Modern Telecommunications, Second Edition
Internet Partner
Gateway Gateway
SS7 SS7
Core Core
Switch Switch
Switches Switches
Core Core
Switch Switch
Edge Routers Edge Routers
Data Center 1 Data Center 2
= Agent-based data collection point
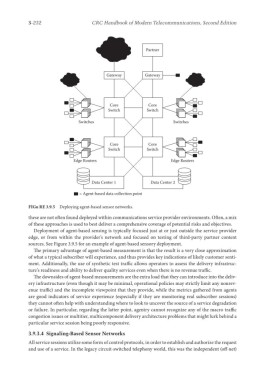
FIGu RE 3.9.5 Deploying agent-based sensor networks.
these are not often found deployed within communications service provider environments. Often, a mix
of these approaches is used to best deliver a comprehensive coverage of potential risks and objectives.
Deployment of agent-based sensing is typically focused just at or just outside the service provider
edge, or from within the provider’s network and focused on testing of third-party partner content
sources. See Figure 3.9.5 for an example of agent-based sensory deployment.
The primary advantage of agent-based measurement is that the result is a very close approximation
of what a typical subscriber will experience, and thus provides key indications of likely customer senti-
ment. Additionally, the use of synthetic test traffic allows operators to assess the delivery infrastruc-
ture’s readiness and ability to deliver quality services even when there is no revenue traffic.
The downsides of agent-based measurements are the extra load that they can introduce into the deliv-
ery infrastructure (even though it may be minimal, operational policies may strictly limit any nonrev-
enue traffic) and the incomplete viewpoint that they provide, while the metrics gathered from agents
are good indicators of service experience (especially if they are monitoring real subscriber sessions)
they cannot often help with understanding where to look to uncover the source of a service degradation
or failure. In particular, regarding the latter point, agentry cannot recognize any of the macro traffic
congestion issues or multitier, multicomponent delivery architecture problems that might lurk behind a
particular service session being poorly responsive.
3.9.3.4 Signaling-Based Sensor Networks
All service sessions utilize some form of control protocols, in order to establish and authorize the request
and use of a service. In the legacy circuit-switched telephony world, this was the independent (off-net)