Page 114 - Hands-On Bug Hunting for Penetration Testers
P. 114
CSRF and Insecure Session Authentication Chapter 6
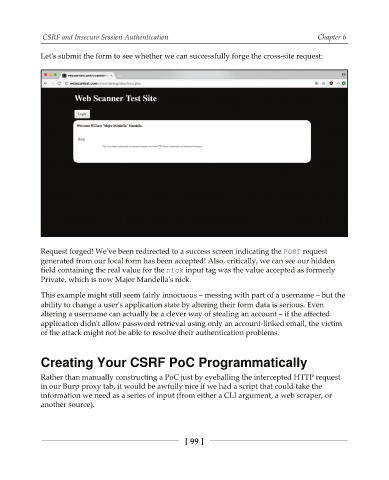
Let's submit the form to see whether we can successfully forge the cross-site request:
Request forged! We've been redirected to a success screen indicating the 1045 request
generated from our local form has been accepted! Also, critically, we can see our hidden
field containing the real value for the OJDL input tag was the value accepted as formerly
Private, which is now Major Mandella's nick.
This example might still seem fairly innocuous d messing with part of a username d but the
ability to change a user's application state by altering their form data is serious. Even
altering a username can actually be a clever way of stealing an account d if the affected
application didn't allow password retrieval using only an account-linked email, the victim
of the attack might not be able to resolve their authentication problems.
Creating Your CSRF PoC Programmatically
Rather than manually constructing a PoC just by eyeballing the intercepted HTTP request
in our Burp proxy tab, it would be awfully nice if we had a script that could take the
information we need as a series of input (from either a CLI argument, a web scraper, or
another source).
[ 99 ]