Page 119 - Hands-On Bug Hunting for Penetration Testers
P. 119
CSRF and Insecure Session Authentication Chapter 6
It looks pretty much like the code we initially wrote from eyeballing the intercepted Burp
request.
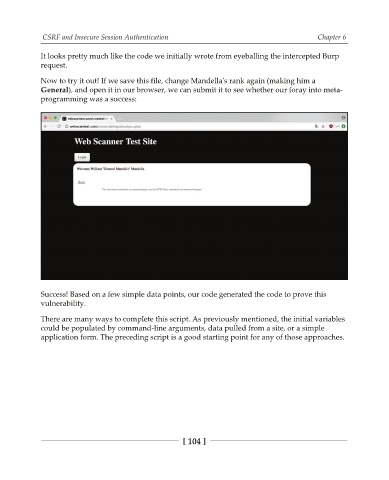
Now to try it out! If we save this file, change Mandella's rank again (making him a
General), and open it in our browser, we can submit it to see whether our foray into meta-
programming was a success:
Success! Based on a few simple data points, our code generated the code to prove this
vulnerability.
There are many ways to complete this script. As previously mentioned, the initial variables
could be populated by command-line arguments, data pulled from a site, or a simple
application form. The preceding script is a good starting point for any of those approaches.
[ 104 ]