Page 171 - Hands-On Bug Hunting for Penetration Testers
P. 171
Framework and Application-Specific Vulnerabilities Chapter 9
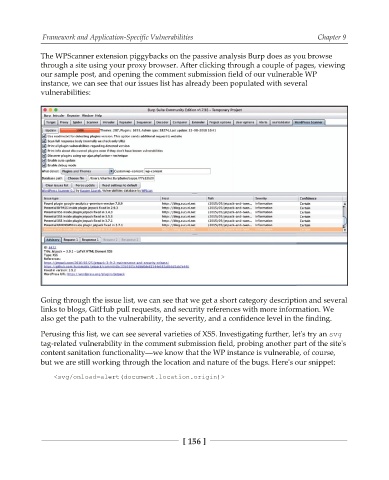
The WPScanner extension piggybacks on the passive analysis Burp does as you browse
through a site using your proxy browser. After clicking through a couple of pages, viewing
our sample post, and opening the comment submission field of our vulnerable WP
instance, we can see that our issues list has already been populated with several
vulnerabilities:
Going through the issue list, we can see that we get a short category description and several
links to blogs, GitHub pull requests, and security references with more information. We
also get the path to the vulnerability, the severity, and a confidence level in the finding.
Perusing this list, we can see several varieties of XSS. Investigating further, let's try an TWH
tag-related vulnerability in the comment submission field, probing another part of the site's
content sanitation functionalitybwe know that the WP instance is vulnerable, of course,
but we are still working through the location and nature of the bugs. Here's our snippet:
TWH POMPBE BMFSU EPDVNFOU MPDBUJPO PSJHJO
[ 156 ]