Page 167 - Hands-On Bug Hunting for Penetration Testers
P. 167
Framework and Application-Specific Vulnerabilities Chapter 9
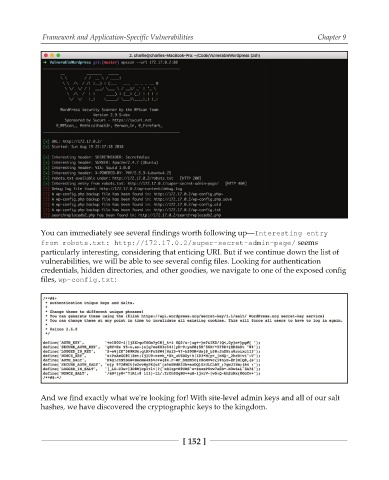
You can immediately see several findings worth following upb*OUFSFTUJOH FOUSZ
GSPN SPCPUT UYU IUUQ TVQFS TFDSFU BENJO QBHF seems
particularly interesting, considering that enticing URI. But if we continue down the list of
vulnerabilities, we will be able to see several config files. Looking for authentication
credentials, hidden directories, and other goodies, we navigate to one of the exposed config
files, XQ DPOGJH UYU:
And we find exactly what we're looking for! With site-level admin keys and all of our salt
hashes, we have discovered the cryptographic keys to the kingdom.
[ 152 ]