Page 126 - StudyBook.pdf
P. 126
110 Chapter 3 • Communication Security: Remote Access and Messaging
TEST DAY TIP
The argument can be made that wireless technologies are part of a local
area network (LAN), not a remote access technology. For the Security+
exam, think of wireless as being a “remote access” because there is no
direct physical (cabled) connection from a laptop, PDA, or smartphone.
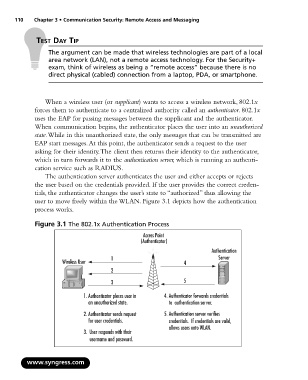
When a wireless user (or supplicant) wants to access a wireless network, 802.1x
forces them to authenticate to a centralized authority called an authenticator. 802.1x
uses the EAP for passing messages between the supplicant and the authenticator.
When communication begins, the authenticator places the user into an unauthorized
state.While in this unauthorized state, the only messages that can be transmitted are
EAP start messages.At this point, the authenticator sends a request to the user
asking for their identity.The client then returns their identity to the authenticator,
which in turn forwards it to the authentication server, which is running an authenti-
cation service such as RADIUS.
The authentication server authenticates the user and either accepts or rejects
the user based on the credentials provided. If the user provides the correct creden-
tials, the authenticator changes the user’s state to “authorized” thus allowing the
user to move freely within the WLAN. Figure 3.1 depicts how the authentication
process works.
Figure 3.1 The 802.1x Authentication Process
Access Point
(Authenticator)
Authentication
1 Server
Wireless User 4
2
3 5
1. Authenticator places user in 4. Authenticator forwards credentials
an unauthorized state. to authentication server.
2. Authenticator sends request 5. Authentication server verifies
for user credentials. credentials. If credentials are valid,
allows users onto WLAN.
3. User responds with their
username and password.
www.syngress.com